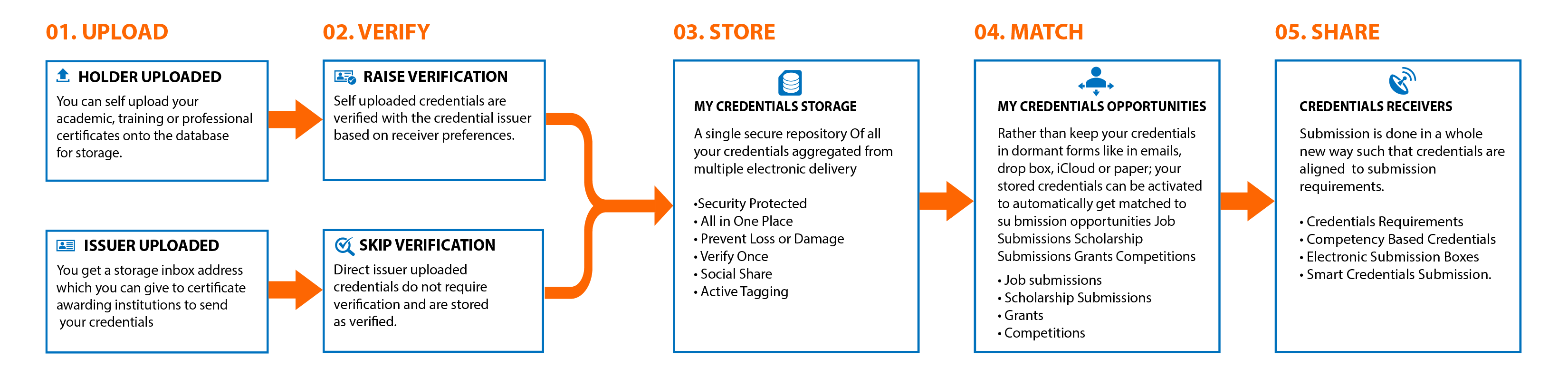
About Us
Holder Services
Receiver Services
There is some connection between players in the credentials value chain, but the relationship is latent.
The credentials value chain starts from the market since they generate demand for skills. Credentials issuing institutions then react to this demand by offering courses and issuing the related credentials to their students who then take it back to the market to find opportunities.
- If a learner has obtained a credential offered as a result of market demand, why would it still be so hard finding and gaining opportunities like Jobs
The challenge is that the players within the credentials value chain (Holders, Issuers, and Receivers) are not properly connected; and in such a way that the full potentials of the credential are realized.
Application requirements are always defined but is vaguely related to the supporting credential
Recruitment agents, staff and admission officers will confirm how difficult, time taken and expensive it is to sift and filter through submitted applications checking for those that meet the defined requirements. It’s so difficult that sometimes schools and companies make an offer is even without the supporting documents to confirm adherence to the requirements.
Because submission requirements are vaguely defined, shortlisting application submission will always be a chore.
Academic credentials submitted for an opportunity are always trusted but sometimes verified.
Academic credential verification is undoubtedly something anyone has to go through at a certain point in their lives. Job hunting aside, it’s also important when moving through certain geographical borders, regardless if it’s for work or study.
But we often find companies that hire staff and tertiary institutions that admit students without verifying the credential that was submitted as a supporting document. This is because the applicants were not required to submit a verified credential.
Academic credentials are stored everywhere; yet dormant
- The students who hold them could have some stored in paper files under the bed, some in emails, some on google drive and the rest on the mobile phone.
- The institutions that issue them could have them stored in paper file rooms, under staff desks or in different staff email boxes and computer folders and the rest unknown.
- The companies and organizations that receive these credentials as part of applications could store them in different staff email boxes or different admission officer folders or stored as paper files in cabinets.
What is common with all these storages is that no one really knows they’re there; because they’re actually just sitting there; dormant.